The treasury operations of a company are crucial, specifically with regard to cash liquidity, which is the most critical aspect. CFOs understand that their treasury teams must mana... Read more
A convergence of geopolitical tensions and climate change concerns is ramping up the pressure for operators to become more efficient in everything they do and wherever they do it—f... Read more
Simplicity and innovation are the foundations on which John ‘Coz’ Colgrove started Pure Storage in 2009. He wanted to keep these principles while achieving a vision to take flash s... Read more
I’m pleased to share that Cisco is announcing its intent to acquire Smartlook, a privately held company headquartered in Brno, Czech Republic. It represents a big step forwar... Read more
Over the last few years the topic of cyber security has moved from the IT department to the board room. The current climate of geopolitical and economic uncertainty has made the th... Read more
Gartner research shows that attack surface expansion is the number one trend for increasing potential cyber threats. Not only that, but according to the Enterprise Strategy Group’s... Read more
A phishing attack is a targeted, fraudulent communication that appears to come from a reputable source. Email phishing occurs when attackers trick legitimate users with proper acce... Read more
Adversary attribution enables security professionals to understand the who, how and why behind the cyberattacks targeting potentially their business. Knowing about espionage-motiva... Read more
When it comes to provisioning the IT on which all businesses rely, running costs and energy efficiency have long played a significant role in the decision-making processes. Recentl... Read more
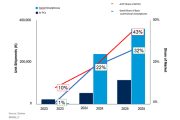
73%, that is the percentage of organisations that have been affected by at least two ransomware attacks in the past year, according to the Veeam Ransomware Trends Report 2022. In m... Read more